TiFRONT ZT Zero Trust
TiFRONT ZT
Security Switch-Based Zero Trust Solution
Start Zero Trust from the Network.
TiFRONT ZT is a Zero Trust security solution that leverages security switches to
implement ultra-fine network segmentation at the user and workload level,
controlling access to resources based on the principle of least privilege.

Internal Threat Propagation — Is Your Enterprise Network Really Safe?
In the past, it was enough to block attacks coming from outside the network. Today, that is no longer sufficient.
Once a threat breaches the internal network, it can silently spread laterally, causing devastating damage
across the entire organization.
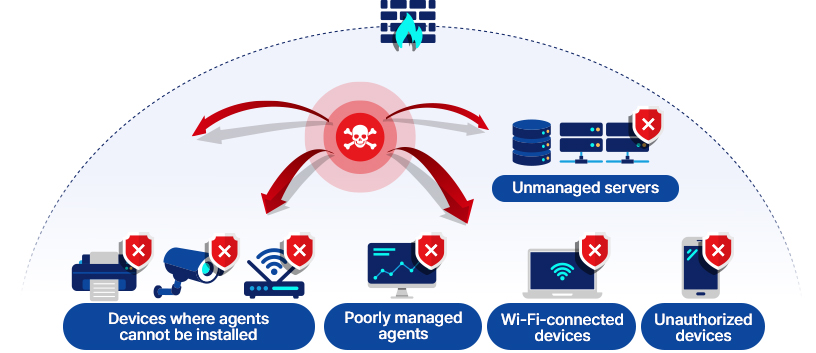
- Ransomware spread
- A single infected PC can rapidly propagate
malware across the entire network.
- Security blind spots
- IoT/OT devices, wireless endpoints, partner
devices, and other agentless systems
become weak points.
- Limitations of perimeter security
- Firewalls alone struggle to detect and control
abnormal internal communications.
- Data leakage
- Stolen privileged accounts or former employees’
accounts can lead to the exposure of
sensitive data.

Attacks will eventually breach the perimeter.
What matters most is stopping lateral movement inside the network.
Network Switches Become the Gateway to Security
Zero Trust must be applied starting from the access network—where user
communications begin—to effectively prevent internal threat propagation.

TiFRONT ZT, the Gateway of Network Security
TiFRONT ZT designates L2/L3 security switches— essential components of any network—as the starting point for security. It enables ultra-fine micro-segmentation at the user and workload level and enforces granular access control based on the principle of least privilege.
Components : TiController ZT(PDP) + TiFRONT Security Switch(PEP)
![]()
- Eliminate Security Blind Spots Without Agents
-
By using network switches as enforcement points, TiFRONT ZT requires no
endpoint agents. It controls all internal communications, including IoT devices,
OT systems, wireless endpoints, and unauthorized devices.
![]()
- Block Lateral Movement Attacks
-
User and device level micro-segmentation prevents attackers from moving
laterally within the internal network. Access to resources is controlled
based on user privileges and device roles.
![]()
- Multi-Layered Internal Network Security
-
Multiple security engines respond to threats at every attack stage—blocking C&C
communications, filtering malicious traffic, and stopping worm propagation.
![]()
- Easy Deployment and Operation
-
Strengthen internal network security simply by replacing existing switches—
no network redesign or agent installation required.
![]()
- Expandable Security Ecosystem
-
Standard REST APIs enable integration with MFA, asset management, antivirus,
EDR/NDR, and other security solutions to extend the Zero Trust architecture.
Complete Network VisibilityEliminate Security Blind Spots
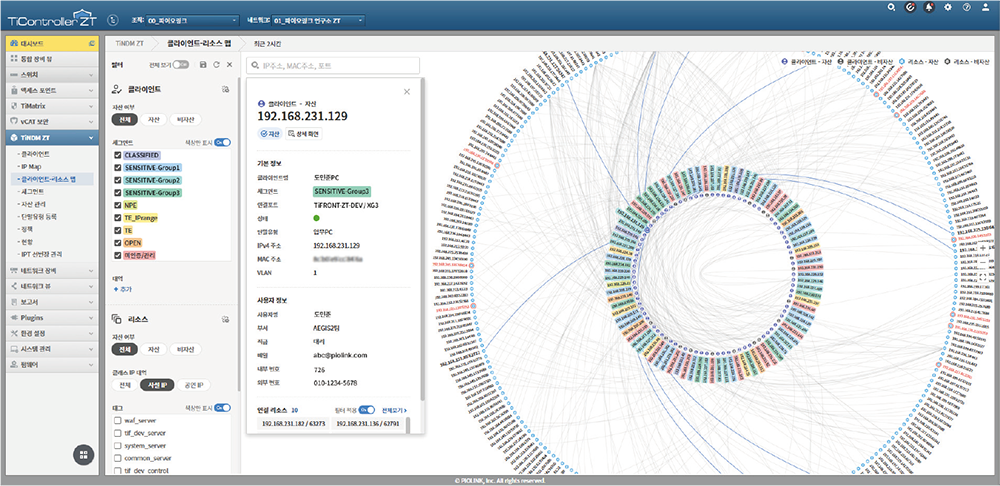
Client-Resource Topology Map
Use security switches as sensors—no agents required.
Visualize real-time client and resource connections in a topology map.
Easily identify and designate “clients” and “resources” based on visualized data.
Reveal hidden threats and ensure transparent security management.
Role-Based Micro-SegmentationEnforce Least Privilege Access
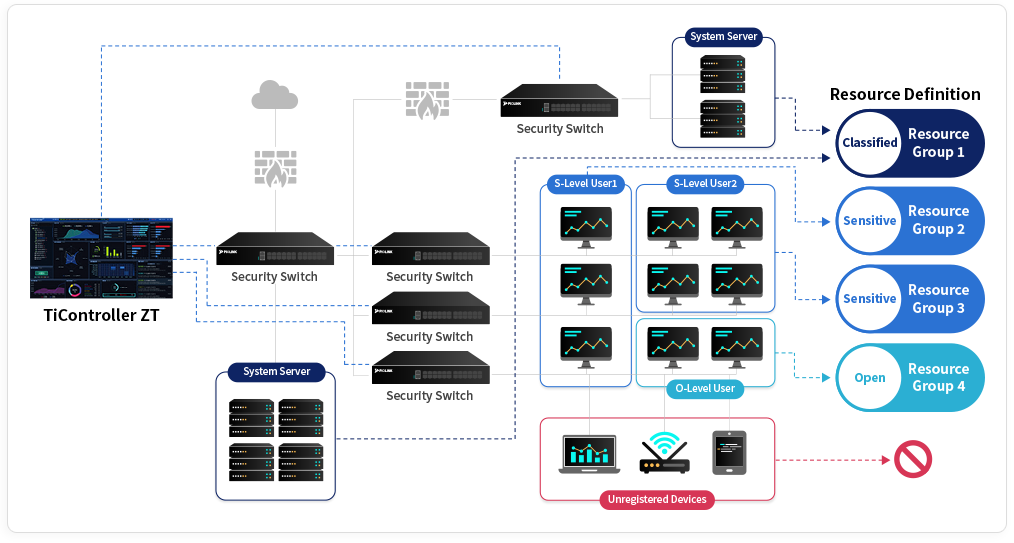
Based on least-privilege policies, TiFRONT ZT implements ultra-fine network segmentation by user role—extending beyond organizational or departmental boundaries down to the workload level.
Prevent lateral movement within the internal network.
Automatically block or isolate unmanaged clients.
Apply least-privilege access policies based on user roles.
Multi-layered Internal Network DefenseContinuous Threat Monitoring & Prevention
-

Threat Site Blocking(CTI Engine)
Predicts threats using PIOLINK’s
Cyber Threat Intelligence and
analysis team. -

Malicious Traffic Blocking(TiMatrix Engine)
Selectively blocks harmful traffic
by analyzing malicious behaviors
such as propagation attacks
and packet interception. -

Worm Propagation Prevention(vCAT Engine)
Detects slow, stealthy attack patterns
and blocks intrusion attempts
at an early stage.
By leveraging multiple security engines, TiFRONT ZT proactively responds to advanced internal threats.
Start Zero Trust from the Network
Zero Trust is a complex security model that cannot be fully implemented overnight.
TiFRONT ZT recommends a phased approach.
- Start with the Network
- Lay the foundation of Zero Trust through network-based micro-
segmentation using security switches.
- Apply the Principle of Least Privilege
- Restrict access so users and devices can reach only the resources
they truly need.
- Design for Scalability
- Begin with a network-centric approach, then gradually expand to
applications, data, and user authentication.
TiFRONT ZT protects every device without blind spots and blocks lateral movement within the internal network.
Just as all communication starts at the switch, security should now start from the network infrastructure.
