Case Studies
Security on university campuses, personal laptops and smart devices (BYOD)
- Customer
-
A university equipped with universities, graduate schools, subsidiary research institutes, etc.
- Challenges
- Block Harmful Traffic Connectivity
IP Management
Centralized Switch Management
Easy management
The university was very vulnerable to campus network security and frequent failures due to students' access to personal laptops and access to smart devices through unauthorized Internet sharing devices.
And the problem was heavy traffic from P2P and Webhard installed to download music and movies.
In a Bring Your Own Device (BYOD) environment, it was difficult to force students to install specific programs on their personal PCs, and it was also difficult to find network failure points.
- Solution
We've replaced it with the TiFRONT on the PIOLINK while maintaining the campus internal network configuration.
TiFRONT is an internal network security and management solution consisting of a cloud security switch and a management system.It centrally manages security-enabled switches on a cloud and web-based basis, providing easy operation, security, △ visibility, and more, including security threat prevention, failover, and visibility into user terminals and traffic usage.Security programs are not required on each user's device, especially for security purposes, and the advantage is that replacing an existing switch with a TiFRONT switch can solve the security problem.The TiFRONT cloud security switch identifies disallowed terminals, falsified IP/MAC devices, and NAT devices to block network access. In addition, in an 802.1X environment, you must pass both user and device authentication before you can apply multiple authentication policies that allow network access.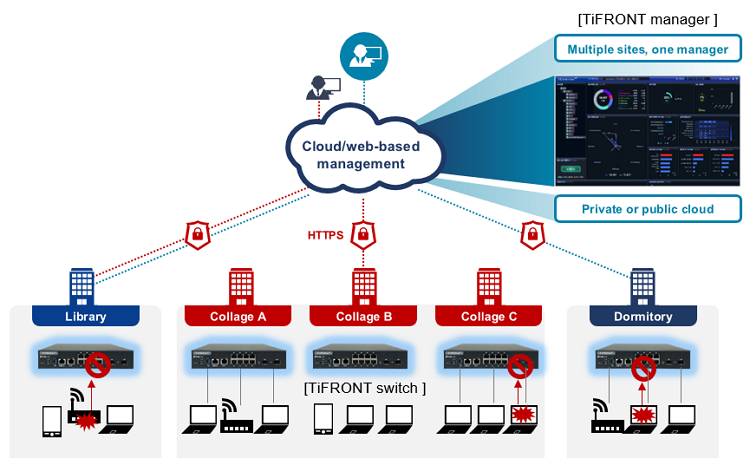
- Benefits
- After the introduction of TiFRONT harmful traffic such as ransomware, botnet, and ARP spoofing was blocked at the switch level, and QoS function provided stable Internet service.
The complex cabling eliminates looping issues and provides a quick, at-a-glance look at the campus network, as well as easy visibility into connected user devices in the management system.
This gives us visibility into our connected user devices, including IP, device type, and traffic usage.
Because traffic usage can be monitored and analyzed on a user-based basis who, when, where, and how much information was sent, excessive traffic priorities such as video traffic were adjusted to prevent network degradation on campus.
